🧠 内存分析:Windows用户密码获取总结
📋 概述
在Windows内存分析中,用户密码相关信息主要存储在以下三个关键位置:
| 存储位置 |
注册表路径 |
包含信息 |
| SAM 注册表 |
HKEY_LOCAL_MACHINE\SAM |
LM Hash、NT Hash |
| SECURITY 注册表 |
HKEY_LOCAL_MACHINE\SECURITY\Policy\Secrets |
系统自动登录密码(LSA Default Password)、DPAPI 密钥(LSA DPAPI secret)等 |
| SYSTEM 注册表 |
HKEY_LOCAL_MACHINE\SYSTEM |
加解密SAM注册表的SYSKEY、加解密LSA Secrets的LSA key |
🎯 核心原理
使用内存分析工具(MemProcFS、Volatility 2、Volatility 3等)获取用户密码相关信息的本质就是读取解析上述三个注册表:
- SAM 注册表解析 → 获取NT Hash → 需要进一步使用cmd5查询或Hashcat爆破获得明文密码
- SECURITY 注册表解析 → 获取系统自动登录密码(LSA Default Password)→ 直接获得明文密码
💡 推荐方案:目前使用 MemProcFS 搭配插件 pym_regsecrets 是内存分析中最快、最稳定、最强大的解决方案。
🔍 方法一:MemProcFS + pym_regsecrets插件(推荐)
✨ 优势特点
MemProcFS的核心功能是将内存镜像挂载成可直接访问的文件系统,使分析人员能够像访问磁盘文件一样访问内存数据,从而提取关键信息、检测恶意软件或进行取证调查。
📥 工具下载
🚀 使用方法
1. 基础挂载命令
1
2
3
4
5
6
7
8
|
memprocfs.exe -device c:\temp\win10x64-dump.raw
memprocfs.exe -device c:\temp\win10x64-dump.raw -v
memprocfs.exe -device c:\temp\win10x64-dump.raw -forensic 1
|
参数说明:
-device : 指定内存转储文件路径-v : 启用详细输出模式-forensic 1 : 开启取证模式,优化对内存中潜在证据的解析
2. 查看密码信息
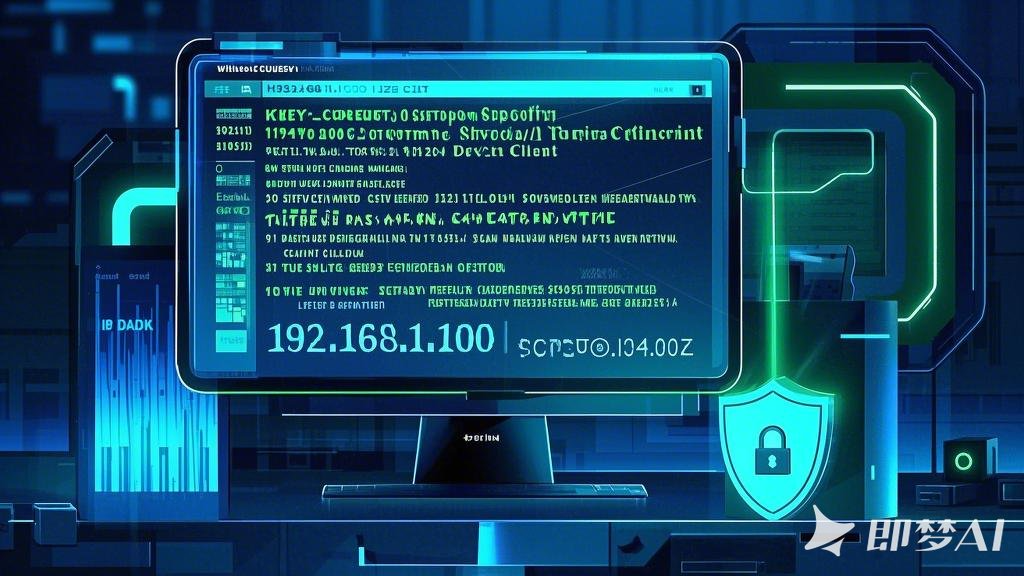
直接访问路径:M:\py\regsecrets\all.txt
📊 输出结果示例
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
| ============== SAM hive secrets ==============
HBoot Key: bf97e59957a794d1a7abfcb0cf4cc04310101010101010101010101010101010
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:17aaf47842c6fde920d9a73ce8868672:::
Forensix:1001:aad3b435b51404eeaad3b435b51404ee:3ad1b677af07545743b72928fd73fd26:::
============== SECURITY hive secrets ==============
Iteration count: 10240
Secrets structure format : VISTA
LSA Key: a02009c2f2f0e2565448d1e4362e47e9a959f81c38099343393506adb4f8f443
NK$LM Key: 40000000000000000000000000000000cecb266207cac6c41ba4e6f4067a6226d29714067f2b55e598b648878bfb880e29046abd78b48b396e49afa717d571350228ae5a1e108765cf5fe8bf27c201c4be5811a72dad870b5eb2ccf03db7fa70
=== LSA Default Password ===
History: True
Username: UNKNOWN
Password: Welc@me_to-MEMORY
=== LSA DPAPI secret ===
History: False
Machine key (hex): 9b4e4b615826aa6b652e66ffc00c49ba51fb378e
User key(hex): 6ea81f12ed9aca5285c596ce6ef5ebbac1668945
=== LSA DPAPI secret ===
History: True
Machine key (hex): 97c30630f083ad266cdffd8c0b54d8718b786eeb
User key(hex): 166225a7aeeedccc1ea0ebb22ab7c22888dcca61
=== LSASecret NL$KM ===
History: False
Secret:
00000000: ce cb 26 62 07 ca c6 c4 1b a4 e6 f4 06 7a 62 26 |..&b.........zb&|
00000010: d2 97 14 06 7f 2b 55 e5 98 b6 48 87 8b fb 88 0e |.....+U...H.....|
00000020: 29 04 6a bd 78 b4 8b 39 6e 49 af a7 17 d5 71 35 |).j.x..9nI....q5|
00000030: 02 28 ae 5a 1e 10 87 65 cf 5f e8 bf 27 c2 01 c4 |.(.Z...e._..'...|
=== LSASecret NL$KM ===
History: True
Secret:
00000000: ce cb 26 62 07 ca c6 c4 1b a4 e6 f4 06 7a 62 26 |..&b.........zb&|
00000010: d2 97 14 06 7f 2b 55 e5 98 b6 48 87 8b fb 88 0e |.....+U...H.....|
00000020: 29 04 6a bd 78 b4 8b 39 6e 49 af a7 17 d5 71 35 |).j.x..9nI....q5|
00000030: 02 28 ae 5a 1e 10 87 65 cf 5f e8 bf 27 c2 01 c4 |.(.Z...e._..'...|
============== SOFTWARE hive secrets ==============
default_logon_user: Forensix
default_logon_domain:
default_logon_password: None
|
🔑 关键信息解读
| 信息类型 |
示例 |
说明 |
| NT Hash |
3ad1b677af07545743b72928fd73fd26 |
从SAM hive secrets中提取,可用于cmd5查询或Hashcat爆破 |
| 明文密码 |
Welc@me_to-MEMORY |
LSA Default Password,直接获得的自动登录明文密码 |
🧰 方法二:Volatility 2
🔓 获取NT Hash
1
| python vol.py -f memory.vmem --profile=Win10x64_19041 hashdump
|
输出示例:
1
2
3
4
| Volatility Foundation Volatility Framework 2.6.1
Administrator:500:aad3b435b51404eeaad3b435b51404ee:481974ce1291ca84c81589a79ee0ff2a:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
CaiXX:1000:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
|
🔐 获取LSA Secrets
1
| python vol.py -f memory.vmem --profile=Win10x64_19041 lsadump
|
输出示例:
1
2
3
4
5
6
7
8
9
10
| Volatility Foundation Volatility Framework 2.6.1
DefaultPassword
0x00000000 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x00000010 83 99 c8 cf 8b 17 25 c4 04 94 52 e4 cc 7f 3a b1 ......%...R...:.
DPAPI_SYSTEM
0x00000000 2c 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ,...............
0x00000010 01 00 00 00 86 f6 78 90 ec 5a cd 60 d2 4b 69 7c ......x..Z.`.Ki|
0x00000020 cb 79 16 d7 67 c5 46 93 ee f9 a0 13 87 c2 ba 49 .y..g.F........I
0x00000030 7a 93 01 58 6f 43 a9 df fd 4f 62 49 00 00 00 00 z..XoC...ObI....
|
🧰 方法三:Volatility 3
🔓 获取NT Hash
1
| python vol.py -f memory.vmem windows.registry.hashdump
|
输出示例:
1
2
3
4
5
6
7
8
| Volatility 3 Framework 2.26.2
Progress: 100.00 PDB scanning finished
User rid lmhash nthash
Administrator 500 aad3b435b51404eeaad3b435b51404ee 31d6cfe0d16ae931b73c59d7e0c089c0
Guest 501 aad3b435b51404eeaad3b435b51404ee 31d6cfe0d16ae931b73c59d7e0c089c0
DefaultAccount 503 aad3b435b51404eeaad3b435b51404ee 31d6cfe0d16ae931b73c59d7e0c089c0
Forensix 1001 aad3b435b51404eeaad3b435b51404ee 3ad1b677af07545743b72928fd73fd26
|
🔐 获取LSA Secrets
1
| python vol.py -f memory.vmem windows.registry.lsadump
|
输出示例:
1
2
3
4
5
6
7
8
9
10
11
12
13
| Volatility 3 Framework 2.26.2
Progress: 100.00 PDB scanning finished
Key Secret Hex
DefaultPassword
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
83 99 c8 cf 8b 17 25 c4 04 94 52 e4 cc 7f 3a b1 ......%...R...:. 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 83 99 c8 cf 8b 17 25 c4 04 94 52 e4 cc 7f 3a b1
DPAPI_SYSTEM
2c 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ,...............
01 00 00 00 86 f6 78 90 ec 5a cd 60 d2 4b 69 7c ......x..Z.`.Ki|
cb 79 16 d7 67 c5 46 93 ee f9 a0 13 87 c2 ba 49 .y..g.F........I
7a 93 01 58 6f 43 a9 df fd 4f 62 49 00 00 00 00 z..XoC...ObI.... 2c 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 01 00 00 00 86 f6 78 90 ec 5a cd 60 d2 4b 69 7c cb 79 16 d7 67 c5 46 93 ee f9 a0 13 87 c2 ba 49 7a 93 01 58 6f 43 a9 df fd 4f 62 49 00 00 00 00
|
🧨 方法四:Mimikatz 离线解密注册表
🔧 前置步骤:挂载内存镜像
1
| memprocfs.exe -device c:\temp\win10x64-dump.raw
|
📁 定位注册表文件
在路径 M:\registry\hive_files\ 下找到以下注册表hive文件:
| 注册表类型 |
文件名格式 |
| SYSTEM |
xxxxxxxxxx-SYSTEM-MACHINE_SYSTEM.reghive |
| SAM |
xxxxxxxxxx-SAM-MACHINE_SAM.reghive |
| SECURITY |
xxxxxxxxxx-SECURITY-MACHINE_SECURITY.reghive |
🔑 Mimikatz 命令操作
1. 获取NT Hash
1
| lsadump::sam /system:SYSTEM注册表路径 /sam:SAM注册表路径
|
完整命令示例:
1
| lsadump::sam /system:"M:\registry\hive_files\0xffffa408dac73000-SYSTEM-MACHINE_SYSTEM.reghive" /sam:"M:\registry\hive_files\0xffffa408e400a000-SAM-MACHINE_SAM.reghive"
|
输出示例:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
| mimikatz # lsadump::sam /system:"M:\registry\hive_files\0xffffa408dac73000-SYSTEM-MACHINE_SYSTEM.reghive" /sam:"M:\registry\hive_files\0xffffa408e400a000-SAM-MACHINE_SAM.reghive"
Domain : DESKTOP-A05J24M
SysKey : 78353ea2f42f5ff4e9179b38fa6c7a5f
Local SID : S-1-5-21-3811590110-1262292590-1806065469
SAMKey : bf97e59957a794d1a7abfcb0cf4cc043
RID : 000001f4 (500)
User : Administrator
RID : 000001f5 (501)
User : Guest
RID : 000001f7 (503)
User : DefaultAccount
RID : 000001f8 (504)
User : WDAGUtilityAccount
Hash NTLM: 17aaf47842c6fde920d9a73ce8868672
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : 36d64ad2e20fc1de0c3929db859a1a70
* Primary:Kerberos-Newer-Keys *
Default Salt : WDAGUtilityAccount
Default Iterations : 4096
Credentials
aes256_hmac (4096) : cd0979355cdfec936ce11d2d736126f8a2f45b5a78a9d862a4441656ebe1a7f2
aes128_hmac (4096) : 3f188cc094cea45c037c815b12214c4e
des_cbc_md5 (4096) : 3d6d1f7a4fdf4383
* Packages *
NTLM-Strong-NTOWF
* Primary:Kerberos *
Default Salt : WDAGUtilityAccount
Credentials
des_cbc_md5 : 3d6d1f7a4fdf4383
RID : 000003e9 (1001)
User : Forensix
Hash NTLM: 3ad1b677af07545743b72928fd73fd26
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : 112b24a01483616d3424c0721e43ca90
* Primary:Kerberos-Newer-Keys *
Default Salt : DESKTOP-A05J24MForensix
Default Iterations : 4096
Credentials
aes256_hmac (4096) : ec37e21ff05d56a785294a4da41028e98b4504a0cc66378a6ffbbc3c181efe04
aes128_hmac (4096) : 2141b8fc2366706369b067805b5e0c11
des_cbc_md5 (4096) : 2fef76a8c24fb0e0
OldCredentials
aes256_hmac (4096) : ec37e21ff05d56a785294a4da41028e98b4504a0cc66378a6ffbbc3c181efe04
aes128_hmac (4096) : 2141b8fc2366706369b067805b5e0c11
des_cbc_md5 (4096) : 2fef76a8c24fb0e0
* Packages *
NTLM-Strong-NTOWF
* Primary:Kerberos *
Default Salt : DESKTOP-A05J24MForensix
Credentials
des_cbc_md5 : 2fef76a8c24fb0e0
OldCredentials
des_cbc_md5 : 2fef76a8c24fb0e0
|
💡 注意:Hash NTLM 对应的值就是NT Hash
2. 获取LSA SECRETS
1
| lsadump::secrets /system:SYSTEM注册表路径 /security:SECURITY注册表路径
|
完整命令示例:
1
| lsadump::secrets /system:"M:\registry\hive_files\0xffffa408dac73000-SYSTEM-MACHINE_SYSTEM.reghive" /security:"M:\registry\hive_files\0xffffa408e445f000-SECURITY-MACHINE_SECURITY.reghive"
|
输出示例:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
| mimikatz # lsadump::secrets /system:"M:\registry\hive_files\0xffffa408dac73000-SYSTEM-MACHINE_SYSTEM.reghive" /security:"M:\registry\hive_files\0xffffa408e445f000-SECURITY-MACHINE_SECURITY.reghive"
Domain : DESKTOP-A05J24M
SysKey : 78353ea2f42f5ff4e9179b38fa6c7a5f
Local name : DESKTOP-A05J24M ( S-1-5-21-3811590110-1262292590-1806065469 )
Domain name : WORKGROUP
Policy subsystem is : 1.18
LSA Key(s) : 1, default {a56e94e3-0c3d-209b-a4c2-7c0774acbfb6}
[00] {a56e94e3-0c3d-209b-a4c2-7c0774acbfb6} a02009c2f2f0e2565448d1e4362e47e9a959f81c38099343393506adb4f8f443
Secret : DefaultPassword
old/text: Welc@me_to-MEMORY
Secret : DPAPI_SYSTEM
cur/hex : 01 00 00 00 9b 4e 4b 61 58 26 aa 6b 65 2e 66 ff c0 0c 49 ba 51 fb 37 8e 6e a8 1f 12 ed 9a ca 52 85 c5 96 ce 6e f5 eb ba c1 66 89 45
full: 9b4e4b615826aa6b652e66ffc00c49ba51fb378e6ea81f12ed9aca5285c596ce6ef5ebbac1668945
m/u : 9b4e4b615826aa6b652e66ffc00c49ba51fb378e / 6ea81f12ed9aca5285c596ce6ef5ebbac1668945
old/hex : 01 00 00 00 97 c3 06 30 f0 83 ad 26 6c df fd 8c 0b 54 d8 71 8b 78 6e eb 16 62 25 a7 ae ee dc cc 1e a0 eb b2 2a b7 c2 28 88 dc ca 61
full: 97c30630f083ad266cdffd8c0b54d8718b786eeb166225a7aeeedccc1ea0ebb22ab7c22888dcca61
m/u : 97c30630f083ad266cdffd8c0b54d8718b786eeb / 166225a7aeeedccc1ea0ebb22ab7c22888dcca61
Secret : NL$KM
cur/hex : ce cb 26 62 07 ca c6 c4 1b a4 e6 f4 06 7a 62 26 d2 97 14 06 7f 2b 55 e5 98 b6 48 87 8b fb 88 0e 29 04 6a bd 78 b4 8b 39 6e 49 af a7 17 d5 71 35 02 28 ae 5a 1e 10 87 65 cf 5f e8 bf 27 c2 01 c4
old/hex : ce cb 26 62 07 ca c6 c4 1b a4 e6 f4 06 7a 62 26 d2 97 14 06 7f 2b 55 e5 98 b6 48 87 8b fb 88 0e 29 04 6a bd 78 b4 8b 39 6e 49 af a7 17 d5 71 35 02 28 ae 5a 1e 10 87 65 cf 5f e8 bf 27 c2 01 c4
|
🎯 重要信息:Secret : DefaultPassword old/text: Welc@me_to-MEMORY 就是自动登录密码
🎉 总结
在Windows内存分析中获取用户密码,推荐首选MemProcFS + pym_regsecrets插件的组合方案,该方案具有操作简单、结果全面、稳定性强的优势,能够同时获取NT Hash和明文密码,是目前最优的解决方案。
.png)